How to set up TinyMDM secure browser on managed devices?
From December 2, 2024, “Internet”, our secure browser will no longer be compatible with Android 7 devices. You therefore have two options:
- You’re using our “Internet” app as your web browser, but not using an Internet protection level (Transparent is selected) : we recommend that you install another web browser, such as Chrome or Firefox, on your policies, since on December 2 the Internet app will no longer work on Android 7 devices.
- You are using our “Internet” application as your web browser and are using an Internet protection level: in this case you will need to install another web browser before December 2, and this will activate our VPN to ensure filtering. It may result in slower use and increased battery consumption.
To continue to benefit from our internet filtering technology integrated directly into our secure “Internet” browser, it’s imperative that you upgrade your fleet of devices to Android 8 or later, or purchase newer devices.
Internet is the secure browser of TinyMDM. It allows, depending on the level of filtering selected in the policy, to restrict internet access on the devices. If you have multiple browsers installed on your devices, please note that the Internet filtering system only works with our secure browser. It is installed by default on the devices as soon as a level of Internet filtering has been triggered in the policy.
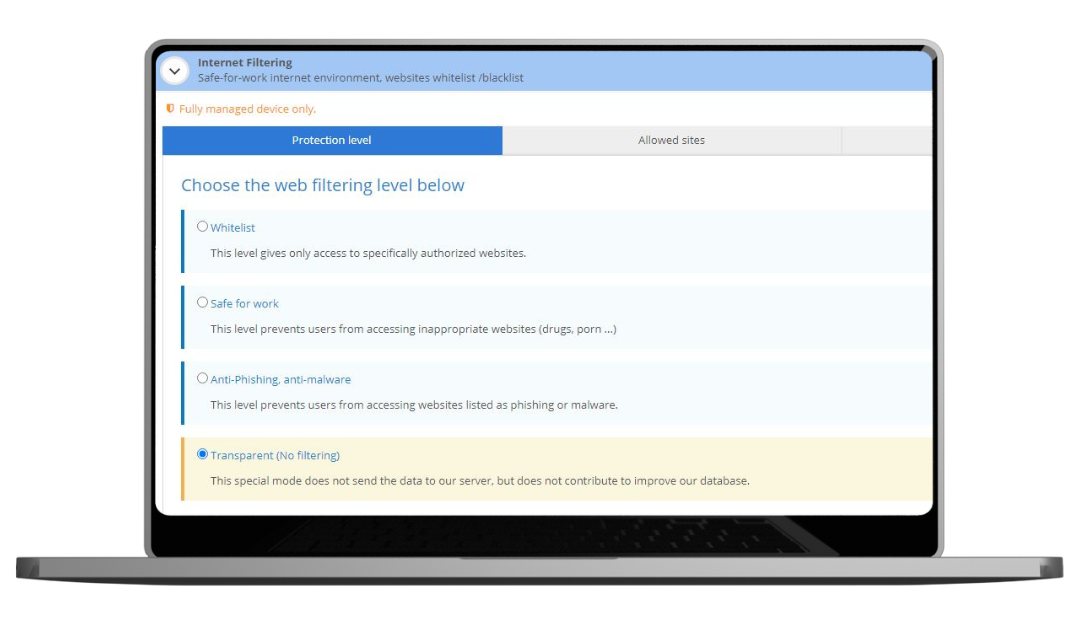
From your policy, you have the possibility to implement 3 different levels of internet filtering. The “Whitelist” filtering restricts access only to sites that have been authorized beforehand. The “Safe for Work” filtering blocks access to any site deemed inappropriate for professional use, while the “Anti-Phishing, anti-malware” filtering prevents access to sites listed as potential sources of phishing or malware. Still on the policy, you can also monitor users’ online activity by accessing the history of visits over the last 15 days. This feature allows you to monitor Internet use, to reinforce network security and prevent potential breaches of the policy.
Note: By activating one of the filtering levels, you launch the automatic installation of TinyMDM’s secure browser. If it is not installed and approved in your policy, you have the option to enable “Use TinyMDM VPN for filtering rather than the integrated secure web browser”. The VPN will take over and filter users’ internet usage. However, if the browser is not installed and the VPN is not activated, internet access will not be filtered.
If the browser is not yet approved and installed on your devices, go to Enterprise Approved Apps and approve the web app Internet ![]() by clicking on ‘Public Apps’. Then type ‘Internet Ars Nova Systems’ in the Play Store search bar, approve it, and install it.
by clicking on ‘Public Apps’. Then type ‘Internet Ars Nova Systems’ in the Play Store search bar, approve it, and install it.
A. If you have an internal website
“In order to avoid accessing misspelled websites, we verify their validity. If you have an internal website, it will be rejected as we cannot access it. To bypass the verification, you need to notify TinyMDM that the website you want to add is an internal website. To do this, you need to prefix the website’s URL with the specified token : intra#
For example: www.myintrawebsite.com should be entered like this intra#www.myintrawebsite.com
B. If you have one or multiple web applications installed 
Web Apps that are approved and installed on TinyMDM work only with Chrome browser. That is why it is important not to delete Chrome even if you want to use Internet ![]() . To avoid users from using Chrome and bypass the Internet filtering system, follow the steps below:
. To avoid users from using Chrome and bypass the Internet filtering system, follow the steps below:
1. In kiosk mode
In your policy, under Apps management, click on the menu ![]() linked to the Chrome application and select Hide app.
linked to the Chrome application and select Hide app.
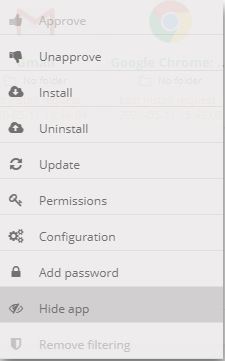
By hiding the app, users will only have access to their web apps on Chrome but they will not be able to visit other websites.
2. In fully managed mode
1. In fully managed mode, it is not possible to hide Chrome. This is why it is important to block access to all the URLs except those of your web applications.
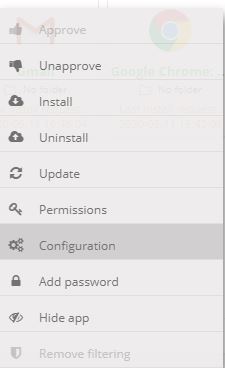
In your policy, under Apps management, click on the menu ![]() linked to Chrome application and select Configuration.
linked to Chrome application and select Configuration.
2. The App managed configurations appear. Search Block access to a list of URLs line and copy-paste the text below:
["https://*", "http://*"]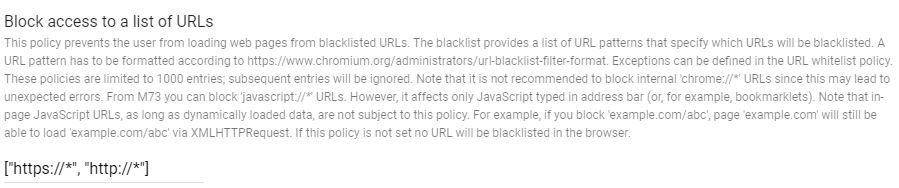
Due to this configuration, users won’t have access to any internet website or any Google research.
3. In order for your web apps to be opened on Chrome, search the Allow access to a list of URLs, above ‘Block access to a list of URLs’.
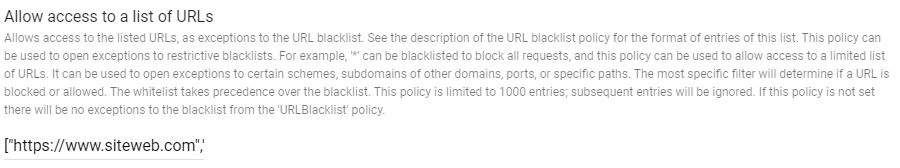
Copy and paste the URLs of your private web apps:
a) If you only have one private web app
Type your private web app’s URL between quotes and square brackets (see example below):
["https://www.siteweb.com"]b) If you have several private web apps
Type the URLs of your web applications one by one. They need to be in quotation marks and separated by a comma. Once you did it, put the entire text in square brackets.
["https://www.siteweb1.com","http://www.siteweb2.fr","http://www.siteweb3.net"]Due to this configuration, clicking on either a web application or the Chrome application will only grant users access to the URLs of authorized private web applications.
